Apr 17, 2024NewsroomEncryption / Vulnerability Threat actors are exploiting unpatched Atlassian servers to deploy a Linux variant of Cerber (aka C3RB3R) ransomware. The attacks leverage CVE-2023-22518 (CVSS score: 9.1), a critical security vulnerability impacting the Atlassian Confluence Data Center and Server that allows an unauthenticated attacker to reset Confluence and create an … [Read more...]
Hackers Exploit Fortinet Flaw, Deploy ScreenConnect, Metasploit in New Campaign
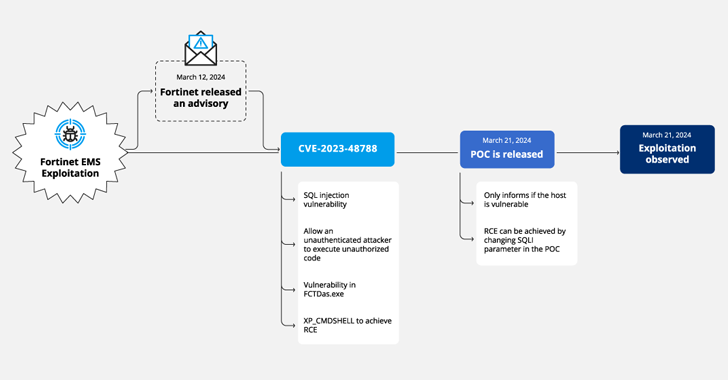
Apr 17, 2024NewsroomVulnerability / Web Application Firewall Cybersecurity researchers have discovered a new campaign that's exploiting a recently disclosed security flaw in Fortinet FortiClient EMS devices to deliver ScreenConnect and Metasploit Powerfun payloads. The activity entails the exploitation of CVE-2023-48788 (CVSS score: 9.3), a critical SQL injection flaw that could permit an … [Read more...]
Cisco Warns of Global Surge in Brute-Force Attacks Targeting VPN and SSH Services
Apr 17, 2024NewsroomIoT Security / Network Security Cisco is warning about a global surge in brute-force attacks targeting various devices, including Virtual Private Network (VPN) services, web application authentication interfaces, and SSH services, since at least March 18, 2024. "These attacks all appear to be originating from TOR exit nodes and a range of other anonymizing tunnels and … [Read more...]
OpenJS Foundation Targeted in Potential JavaScript Project Takeover Attempt
Apr 16, 2024NewsroomSupply Chain / Software Security Security researchers have uncovered a "credible" takeover attempt targeting the OpenJS Foundation in a manner that evokes similarities to the recently uncovered incident aimed at the open-source XZ Utils project. "The OpenJS Foundation Cross Project Council received a suspicious series of emails with similar messages, bearing different names … [Read more...]
TA558 Hackers Weaponize Images for Wide-Scale Malware Attacks
Apr 16, 2024NewsroomThreat Intelligence / Endpoint Security The threat actor tracked as TA558 has been observed leveraging steganography as an obfuscation technique to deliver a wide range of malware such as Agent Tesla, FormBook, Remcos RAT, LokiBot, GuLoader, Snake Keylogger, and XWorm, among others. "The group made extensive use of steganography by sending VBSs, PowerShell code, as well as … [Read more...]
AWS, Google, and Azure CLI Tools Could Leak Credentials in Build Logs
Apr 16, 2024NewsroomCloud Security / DevSecOps New cybersecurity research has found that command-line interface (CLI) tools from Amazon Web Services (AWS) and Google Cloud can expose sensitive credentials in build logs, posing significant risks to organizations. The vulnerability has been codenamed LeakyCLI by cloud security firm Orca. "Some commands on Azure CLI, AWS CLI, and Google Cloud CLI … [Read more...]
Widely-Used PuTTY SSH Client Found Vulnerable to Key Recovery Attack
Apr 16, 2024NewsroomEncryption / Network Security The maintainers of the PuTTY Secure Shell (SSH) and Telnet client are alerting users of a critical vulnerability impacting versions from 0.68 through 0.80 that could be exploited to achieve full recovery of NIST P-521 (ecdsa-sha2-nistp521) private keys. The flaw has been assigned the CVE identifier CVE-2024-31497, with the discovery credited to … [Read more...]
Identity in the Shadows: Shedding Light on Cybersecurity's Unseen Threats
Apr 16, 2024The Hacker NewsCloud Security / Threat Intelligence In today's rapidly evolving digital landscape, organizations face an increasingly complex array of cybersecurity threats. The proliferation of cloud services and remote work arrangements has heightened the vulnerability of digital identities to exploitation, making it imperative for businesses to fortify their identity security … [Read more...]
FTC Fines Mental Health Startup Cerebral $7 Million for Major Privacy Violations
Apr 16, 2024NewsroomPrivacy Breach / Regulatory Compliance The U.S. Federal Trade Commission (FTC) has ordered the mental telehealth company Cerebral from using or disclosing personal data for advertising purposes. It has also been fined more than $7 million over charges that it revealed users' sensitive personal health information and other data to third parties for advertising purposes and … [Read more...]
Hive RAT Creators and $3.5M Cryptojacking Mastermind Arrested in Global Crackdown
Two individuals have been arrested in Australia and the U.S. in connection with an alleged scheme to develop and distribute a remote access trojan called Hive RAT (previously Firebird). The U.S. Justice Department (DoJ) said the malware "gave the malware purchasers control over victim computers and enabled them to access victims' private communications, their login credentials, and other personal … [Read more...]
Intel and Lenovo BMCs Contain Unpatched Lighttpd Server Flaw
Apr 15, 2024NewsroomFirmware Security / Vulnerability A security flaw impacting the Lighttpd web server used in baseboard management controllers (BMCs) has remained unpatched by device vendors like Intel and Lenovo, new findings from Binarly reveal. While the original shortcoming was discovered and patched by the Lighttpd maintainers way back in August 2018 with version 1.4.51, the lack of a CVE … [Read more...]
AI Copilot: Launching Innovation Rockets, But Beware of the Darkness Ahead
Imagine a world where the software that powers your favorite apps, secures your online transactions, and keeps your digital life could be outsmarted and taken over by a cleverly disguised piece of code. This isn't a plot from the latest cyber-thriller; it's actually been a reality for years now. How this will change – in a positive or negative direction – as artificial intelligence (AI) takes on a … [Read more...]
Muddled Libra Shifts Focus to SaaS and Cloud for Extortion and Data Theft Attacks
Apr 15, 2024NewsroomCloud Security /SaaS Security The threat actor known as Muddled Libra has been observed actively targeting software-as-a-service (SaaS) applications and cloud service provider (CSP) environments in a bid to exfiltrate sensitive data. "Organizations often store a variety of data in SaaS applications and use services from CSPs," Palo Alto Networks Unit 42 said in a report … [Read more...]
Timing is Everything: The Role of Just-in-Time Privileged Access in Security Evolution
Apr 15, 2024The Hacker NewsActive Directory / Attack Surface To minimize the risk of privilege misuse, a trend in the privileged access management (PAM) solution market involves implementing just-in-time (JIT) privileged access. This approach to privileged identity management aims to mitigate the risks associated with prolonged high-level access by granting privileges temporarily and only when … [Read more...]
Chinese-Linked LightSpy iOS Spyware Targets South Asian iPhone Users
Apr 15, 2024NewsroomSpyware / Mobile Security Cybersecurity researchers have discovered a "renewed" cyber espionage campaign targeting users in South Asia with the aim of delivering an Apple iOS spyware implant called LightSpy. "The latest iteration of LightSpy, dubbed 'F_Warehouse,' boasts a modular framework with extensive spying features," the BlackBerry Threat Research and Intelligence Team … [Read more...]
Palo Alto Networks Releases Urgent Fixes for Exploited PAN-OS Vulnerability
Apr 15, 2024NewsroomFirewall Security / Vulnerability Palo Alto Networks has released hotfixes to address a maximum-severity security flaw impacting PAN-OS software that has come under active exploitation in the wild. Tracked as CVE-2024-3400 (CVSS score: 10.0), the critical vulnerability is a case of command injection in the GlobalProtect feature that an unauthenticated attacker could weaponize … [Read more...]
Ex-Security Engineer Jailed 3 Years for $12.3 Million Crypto Exchange Thefts
Apr 13, 2024NewsroomCryptocurrency / Regulatory Compliance A former security engineer has been sentenced to three years in prison in the U.S. for charges relating to hacking two decentralized cryptocurrency exchanges in July 2022 and stealing over $12.3 million. Shakeeb Ahmed, the defendant in question, pled guilty to one count of computer fraud in December 2023 following his arrest in July. "At … [Read more...]
U.S. Treasury Hamas Spokesperson for Cyber Influence Operations
Apr 13, 2024NewsroomCyber influence / Warfare The U.S. Treasury Department's Office of Foreign Assets Control (OFAC) on Friday announced sanctions against an official associated with Hamas for his involvement in cyber influence operations. Hudhayfa Samir 'Abdallah al-Kahlut, 39, also known as Abu Ubaida, has served as the public spokesperson of Izz al-Din al-Qassam Brigades, the military wing of … [Read more...]
Hackers Deploy Python Backdoor in Palo Alto Zero-Day Attack
Apr 13, 2024Newsroom Threat actors have been exploiting the newly disclosed zero-day flaw in Palo Alto Networks PAN-OS software dating back to March 26, 2024, nearly three weeks before it came to light yesterday. The network security company's Unit 42 division is tracking the activity under the name Operation MidnightEclipse, attributing it as the work of a single threat actor of unknown … [Read more...]
Popular Rust Crate liblzma-sys Compromised with XZ Utils Backdoor Files
"Test files" associated with the XZ Utils backdoor have made their way to a Rust crate known as liblzma-sys, new findings from Phylum reveal. liblzma-sys, which has been downloaded over 21,000 times to date, provides Rust developers with bindings to the liblzma implementation, an underlying library that is part of the XZ Utils data compression software. The impacted version in question is … [Read more...]
- « Previous Page
- 1
- 2
- 3
- 4
- 5
- …
- 101
- Next Page »