A little over two years have passed since the online vigilante who would call himself P4x fired the first shot in his own one-man cyberwar. Working alone in his coastal Florida home in late January of 2022, wearing slippers and pajama pants and periodically munching on Takis corn snacks, he spun up a set of custom-built programs on his laptop and a collection of cloud-based servers that … [Read more...]
The Mystery of ‘Jia Tan,’ the XZ Backdoor Mastermind
The scourge of software supply chain attacks—an increasingly common hacking technique that hides malicious code in a widely used legitimate program—can take many forms. Hackers can penetrate an update server to seed out their malware, or even break into the network where the software was developed to corrupt it at the source. Or, in the case of one particularly insidious software supply chain … [Read more...]
The XZ Backdoor: Everything You Need to Know
On Friday, a lone Microsoft developer rocked the world when he revealed a backdoor had been intentionally planted in XZ Utils, an open source data compression utility available on almost all installations of Linux and other Unix-like operating systems. The person or people behind this project likely spent years on it. They were likely very close to seeing the backdoor update merged into Debian and … [Read more...]
The Incognito Mode Myth Has Fully Unraveled
If you still hold any notion that Google Chrome’s “Incognito mode” is a good way to protect your privacy online, now’s a good time to stop.Google has agreed to delete “billions of data records” the company collected while users browsed the web using Incognito mode, according to documents filed in federal court in San Francisco on Monday. The agreement, part of a settlement in a class action … [Read more...]
A Ghost Ship’s Doomed Journey Through the Gate of Tears
The ballistic missile hit the Rubymar on the evening of February 18. For months, the cargo ship had been shuttling around the Arabian Sea, uneventfully calling at local ports. But now, taking on water in the bottleneck of the Bab-el-Mandeb Strait, its two dozen crew issued an urgent call for help and prepared to abandon ship.Over the next two weeks—while the crew were ashore—the “ghost ship” took … [Read more...]
You Should Update Apple iOS and Google Chrome ASAP
It’s time to check your software updates. March has seen the release of important patches for Apple’s iOS, Google’s Chrome, and its privacy-conscious competitor Firefox. Bugs have also been squashed by enterprise software giants including Cisco, VMware, and SAP.Here’s what you need to know about the security updates issued in March.Apple iOSApple made up for a quiet February by issuing two … [Read more...]
Yogurt Heist Reveals a Rampant Form of Online Fraud
The saga of WikiLeaks founder Julian Assange continued this week after the UK’s high court ordered a delay in his extradition to the United States. Assange faces 18 charges in the US, including 17 alleged violations of the Espionage Act—charges that have alarmed journalism watchdogs. The two judges who issued the ruling said in a summary of their decision that the US must offer further assurances … [Read more...]
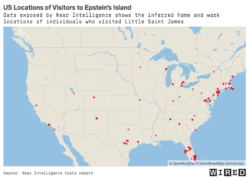
Jeffrey Epstein's Island Visitors Exposed by Data Broker
Nearly 200 mobile devices of people who visited Jeffrey Epstein’s notorious “pedophile island” in the years prior to his death left an invisible trail of data pointing back to their own homes and offices. Maps of these visitations generated by a troubled international data broker with defense industry ties, discovered last week by WIRED, document the numerous trips of wealthy and influential … [Read more...]
‘Malicious Activity’ Hits the University of Cambridge’s Medical School
The University of Cambridge is constantly ranked among the world’s top universities, with its medical school and vast research facilities among the very best. But for the past month, staff at the prestigious medical school have had work hampered following “malicious activity” on its computer network.An emailed “staff notice” seen by WIRED, believed to have been sent at the end of February, alerted … [Read more...]
Julian Assange Won’t Be Extradited to the US Yet
The UK high court has extended WikiLeaks founder Julian Assange’s hope to avoid espionage charges in the United States, allowing Assange to further challenge his extradition from the UK to the US.In a ruling issued in London on Tuesday, two high court judges said that Assange will not be immediately extradited to the United States. In a press summary of the 60-page decision, the court said Assange … [Read more...]
Chinese Hackers Charged in Decade-Long Global Spying Rampage
For years, China’s state-backed hackers have stolen huge troves of company secrets, political intelligence, and the personal information of millions of people. On Monday, officials in the United States and United Kingdom expanded the long list of hacking allegations, claiming China is responsible for breaching the UK’s elections watchdog and accessing 40 million people’s data. The countries also … [Read more...]
Apple Chip Flaw Leaks Secret Encryption Keys
The next time you stay in a hotel, you may want to use the door’s deadbolt. A group of security researchers this week revealed a technique that uses a series of security vulnerabilities that impact 3 million hotel room locks worldwide. While the company is working to fix the issue, many of the locks remain vulnerable to the unique intrusion technique.Apple is having a tough week. In addition to … [Read more...]
Apple's iMessage Encryption Puts Its Security Practices in the DOJ's Crosshairs
For well over a decade, Apple has been praised by privacy advocates for its decision in 2011 to end-to-end encrypt iMessage, securing users' communications on the default texting app for all its devices so thoroughly that even Apple itself can't read their messages. Years before WhatsApp switched on end-to-end encryption in 2016, and before Signal—now widely considered the most private end-to-end … [Read more...]
Hackers Found a Way to Open Any of 3 Million Hotel Keycard Locks in Seconds
When thousands of security researchers descend on Las Vegas every August for what's come to be known as “hacker summer camp,” the back-to-back Black Hat and Defcon hacker conferences, it's a given that some of them will experiment with hacking the infrastructure of Vegas itself, the city's elaborate array of casino and hospitality technology. But at one private event in 2022, a select group of … [Read more...]
Some of the Most Popular Websites Share Your Data With Over 1,500 Companies
Everywhere you go online, you’re being tracked. Almost every time you visit a website, trackers gather data about your browsing and funnel it back into targeted advertising systems, which build up detailed profiles about your interests and make big profits in the process. In some places, you’re tracked more than others.In a little-noticed change at the end of last year, thousands of websites … [Read more...]
Glassdoor Wants to Know Your Real Name
Using Glassdoor, the site famous for candid employee reviews that break through corporate facades, is less anonymous than it used to be.In July last year, the company added new social features integrated from Fishbowl, an app for work-related discussions acquired in 2021. Glassdoor has also changed its sign-up process to ask people to disclose their full name, job title, and employer; … [Read more...]
Automakers Are Telling Your Insurance Company How You Really Drive
How do you know the internet has a deepfake porn problem? Just look at copyright takedown requests. WIRED found this week that Google is receiving thousands of Digital Millennium Copyright Act complaints for deepfake nudes, most of which are published by just a handful of websites. Experts say the deluge of DMCA takedown requests is evidence that Google should delist the offending sites from … [Read more...]
Sinking Section 702 Wiretap Program Offered One Last Lifeboat
A bill introduced by senators Dick Durbin and Mike Lee to reauthorize the Section 702 surveillance program is the fifth introduced in the US Congress this winter. The authority is threatening to expire in a month, disrupting a global wiretapping program said to inform a third of articles in the President’s Daily Briefing—a morning “tour d’horizon” of US spies’ top concerns.But the stakes aren't … [Read more...]
The ‘Emergency Powers’ Risk of a Second Trump Presidency
Donald Trump appears to dream of being an American authoritarian should he return to office. The former US president, who on Tuesday secured enough delegates to win the 2024 Republican nomination, plans to deport millions of undocumented immigrants and house scores of them in large camps. He wants to invoke the Insurrection Act to deploy the military in cities across the nation to quell civil … [Read more...]
There Are Dark Corners of the Internet. Then There's 764
WIRED collaborated with Der Spiegel, Recorder, and The Washington Post on this reporting. Each wrote separate stories that the news organizations agreed to publish in tandem. This story contains descriptions of abuse, self-harm, murder, and suicide. Reader discretion is advised.It sounds like a cheap true-crime conspiracy: An international network of predators steeped in Satanism lure children … [Read more...]
- « Previous Page
- 1
- 2
- 3
- 4
- …
- 27
- Next Page »